Our Services
Accelerate your business success with our innovative digital solutions.
Case Studies

Transit Rewards
Public Transport
Transit Rewards is a mobile app for commuters and all public transport in Canada, promoting a carbon-free environment. It follows a reward-based system where passengers get points for traveling by public transport.

My Dasma
E-commerce Marketplace
MyDasma is a mobile and web application bridging the link between couples (to be) and wedding planners.

CaseFunder
Fintech
An Innovative Platform for Anonymous Borrowers and Lenders

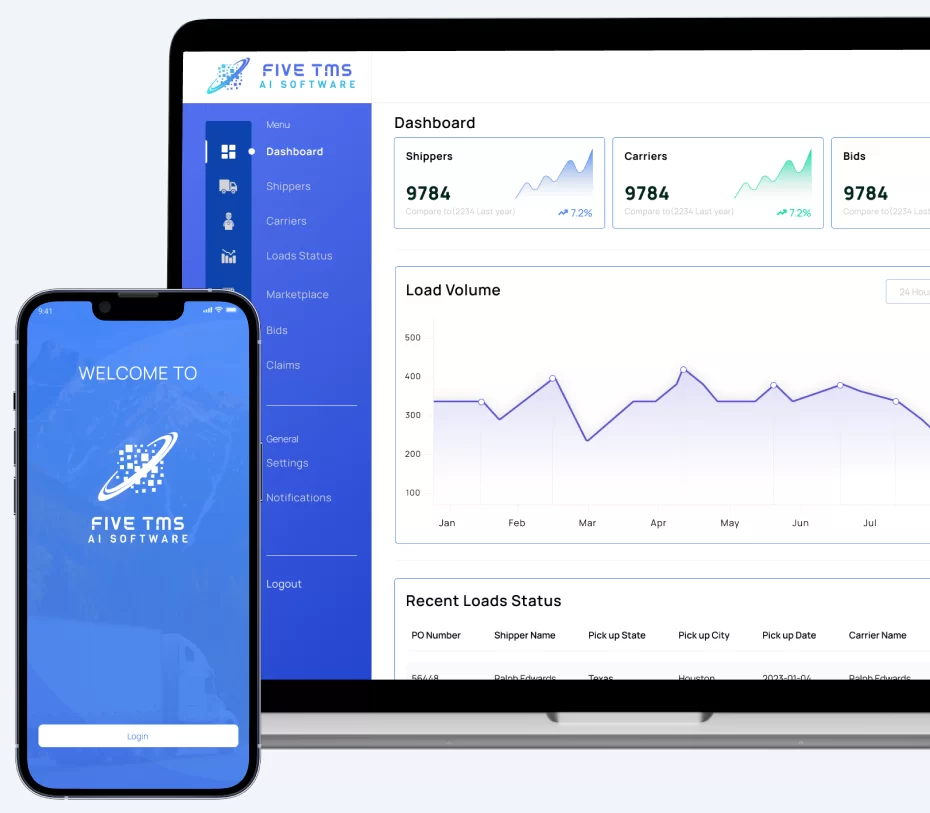
Property Management System
An ultimate property management system that offers a multi-portal approach to simplify the property management process.
Unlock your business potential with our expert outsourcing solutions
We offer an extension to your in-house team by thoughtfully curating the perfect team members for each task and project. With us, you can access a team of skilled designers, developers, and project managers, without the hassle of managing full-time employees.
Why our clients
love us?
Our clients love us because we prioritize effective communication and are committed to delivering high-quality software solutions that meet the highest standards of excellence.
Ready to discuss your Cross-Platform App development project? Get in touch today to get started.
"*" indicates required fields
Our Technology Stack

Our Achievements
Top Software Development
Companies in Pakistan for 2024
Check our profile at Clutch
Our Partners
Brands We've Worked With

Custom Software

Web Development
App Development

Web Development

Web Development

Web Development

Web Development
Web Development

Web Development

E-commerce Development

Web Development

Product Development

Web Development




